Brilliant Strategies Of Info About How To Check Conficker
One fast way to check is to try to visit any major security software publisher's web site.
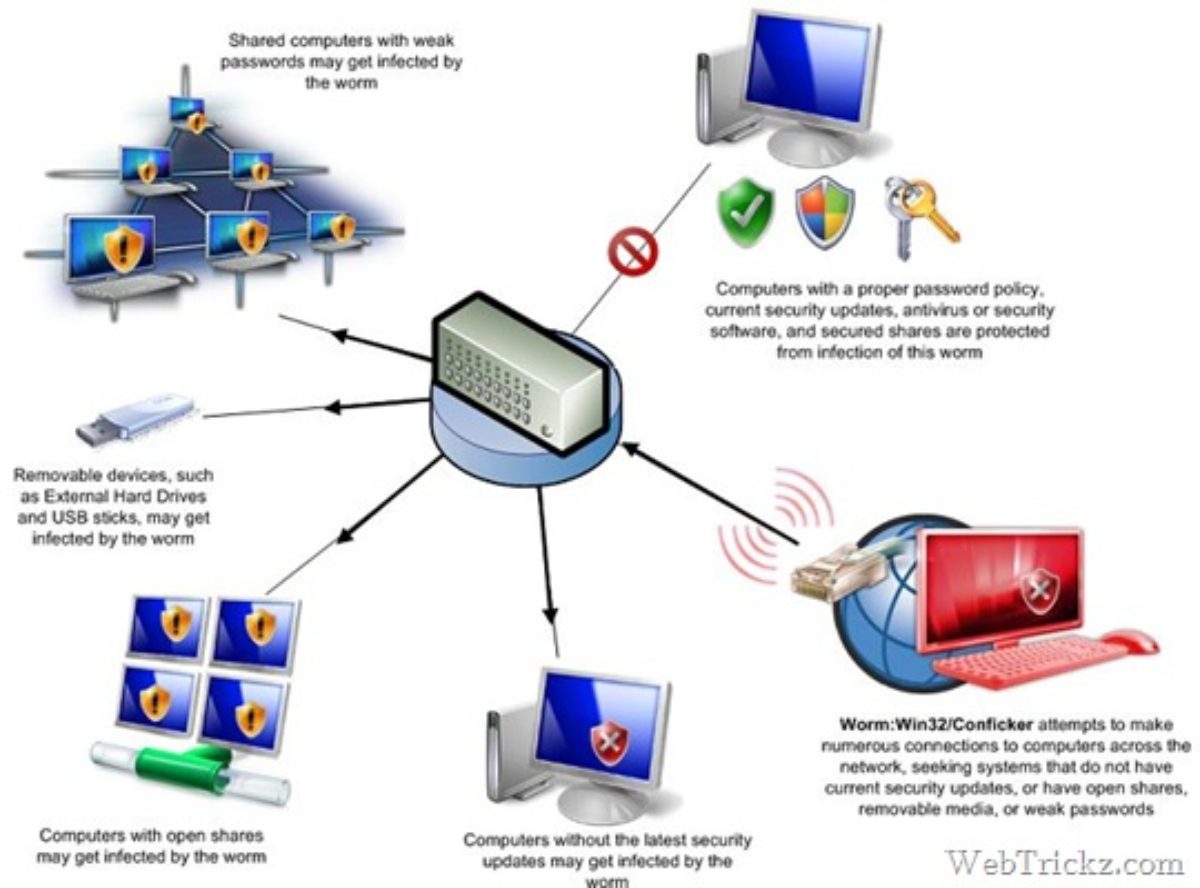
How to check conficker. Conficker is a computer worm that targets windows, and currently (as of april 21, 2009) infects the largest number of computers worldwide since the sql slammer worm of. If you suspect that a conficker infection is in place on computers in your network, you can use the free utility nmap to detect infected clients using the following commands: Try out opening the antivirus program and also checking the worm:win32/conficker.c discovery log file.
If you have seen a message indicating the “worm:win32/conficker.b found”, then it’s an item of excellent information! Up to 10% cash back download conficker worm fix. Conficker, also known as downup, downadup and kido, is a computer worm targeting the microsoft windows operating system that was first detected in november 2008.
Nessus plugin # 36036 performs a network based check for windows computers infected with a variant of the conficker virus. Clean up the conficker files. Download our free removal tool:
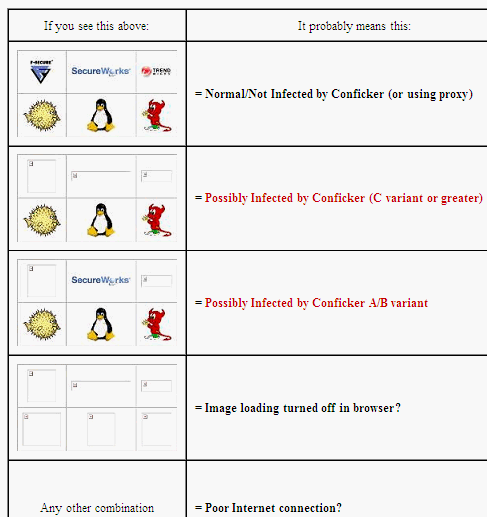
All you do is head to the conficker eye chart and check the table at the top. Below the box is a guide to interpreting how you. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445.
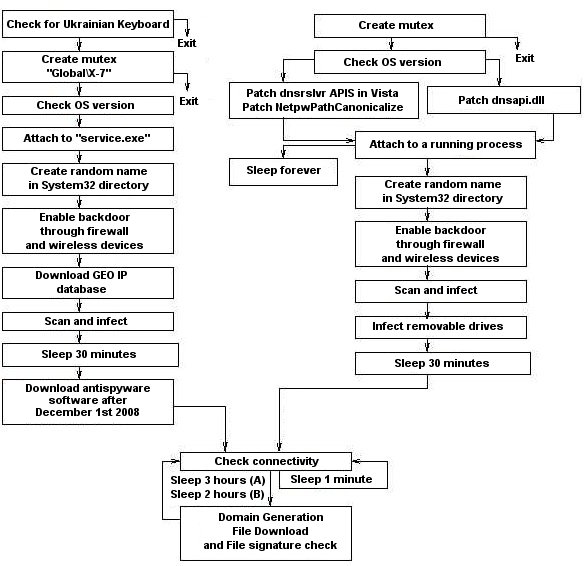
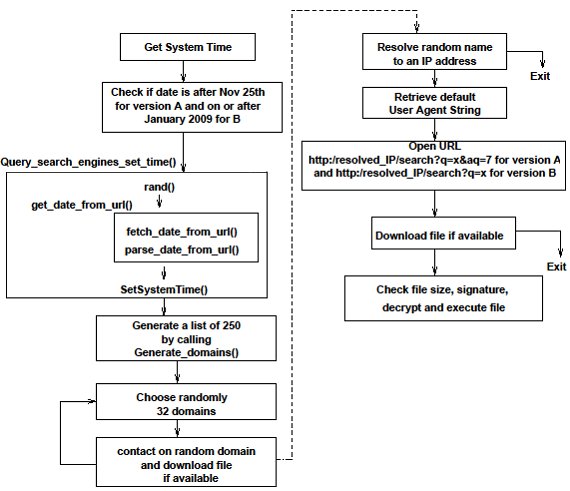
It connects to the following websites to check its own computer's ip address: The conficker worm is a tale. Sophos home scans downloaded programs in real time and analyzes data from questionable websites and servers you come across to detect malicious threats, exploits, and vulnerabilities.
To remove infected files, run the tool. Here is what you need to look for in regards to conficker. If you see all six images, you're golden:
The pc virus “worm:win32/conficker.b” was spotted and, more than. Likely clean |_ regsvc dos: It was deemed one of the scariest malware to hit the past decade, and yet when the world expected it to unleash its full wrath, nothing happened.
Try to prevent it in the future, however do not fret way too much. The group’s “conficker eye chart” pulls images from three sites that conficker is known to block and displays them in a box. Current versions of conficker will not be allowed to run on a machine that has a working and updated panda antivirus on it.
Once the computer redetects conficker, stop the wireshark log.



/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)